Hacking/Cracking
Hacking/Cracking

What is a Hacker?
A hacker, in the modern
day, is a person with great technical knowledge of how computers work and transmit
data. Hackers are typically well versed in computer languages, and able to code
their own programs for whatever purposes they have in mind. Hackers may choose
to covertly infiltrate secure systems, look at some data, and leave with the
system intact. Hackers claim their intentions to be benevolent; most of them
simply find the challenge of hacking to be a reward in and of itself, and many
more simply wish for information to be free.
What is a Cracker?
A cracker, simply put, is a destructive and malevolent hacker. Crackers infiltrate systems for the purpose of destroying critical or non-critical data, defacing public web pages, attaining sensitive data for profit or other non-educational purposes, breaking protection schemes on copyrighted programs, and so on.
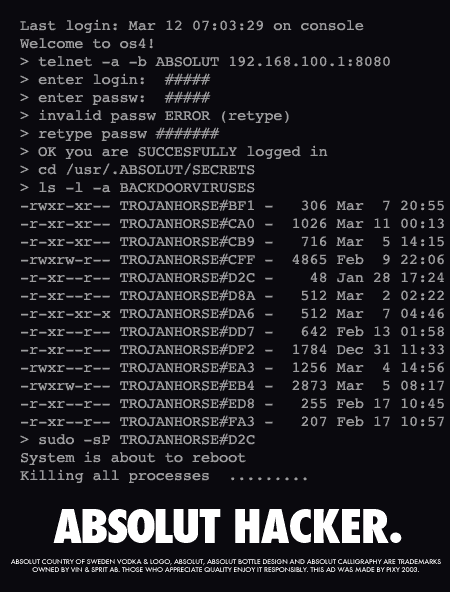
How and why do people generally go about hacking and cracking?
Hacking and cracking follow the same
procedures; it's what is done with the information that differentiates the two.
Generally, hackers/crackers employ password cracking tools to bypass encrypted
passwords, or passwords scrambled in some way as to render them unreadable by
plain text methods. Hackers can also use social engineering to get password
data out of unwitting parties. For a more detailed explanation, check out this
article by IBM's security team. Hackers might hack to free information or
expose security vulnerabilities that they feel a company should address; crackers
generally do their work for personal amusement or profit, with disregard to
the data they are damaging. For some examples of how hacking has shaped the
world of the Internet, take a look at this
story about the hacking of al-Jazeera's website during the Iraq war, and
this article
about the hacking of the RIAA's website over file sharing.
What are the ethical concerns for both hackers and crackers?
Obviously, cracking is immoral and unethical.
The data they damage is considered to be private, secure, and the property of
whoever created it or owns the servers it is stored on. Hacking is a more sensitive
issue. On the one hand, there is no harmful intent, and in the vast majority
of cases no damage done. On the other hand, the data is still private, the system
was still infiltrated by someone who did not have permission to do so, and there
could be unintentional
damage done if the hacker is not careful. Any unauthorized infiltration
of a secure, private system is illegal, as is any damage caused for any reason.
The hacker has to make a judgment call before beginning his work: is it worth
the risk? Can I justify to myself the risks involved in face of the legal prohibition?
Program Cracking Misuse of Information