802.11 Data Link Layer
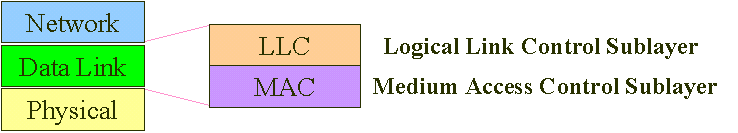
Fig.1 Data Link Layer
The data link layer within 802.11 consists of two sublayers: Logical Link Control (LLC) and Media Access Control (MAC). 802.11 uses the same 802.2 LLC and 48-bit addressing as other 802 LANs, allowing for very simple bridging from wireless to IEEE wired networks, but the MAC is unique to WLANs.
The 802.11 MAC is very similar in concept to 802.3, in that it is designed to support multiple users on a shared medium by having the sender sense the medium before accessing it. For 802.3 Ethernet LANs, the Carrier Sense Multiple Access with Collision Detection (CSMA/CD) protocol regulates how Ethernet stations establish access to the wire and how they detect and handle collisions that occur when two or more devices try to simultaneously communicate over the LAN.
Why we need different MAC from wired LAN?
Reason One: "near/far" problem: To detect a collision, a station must be able to transmit and listen at the same time, but in an 802.11 WLAN, the transmission of radio systems drowns out the ability of the station to “hear?a collision.
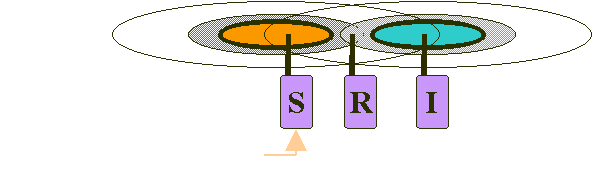
Fig.2 "near/far" problem, in which S can not "hear" collision at R
Reason Two: "hidden node" issue, in which two stations on opposite sides of an access point can both “hear?activity from an access point, but not from each other, usually due to distance or an obstruction.
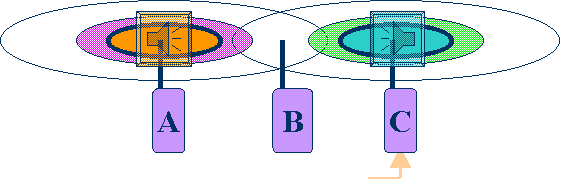
Fig.3 "hidden node" problem: when A is transmitting, C can not detect it's activity, thus C is not able to sense the carrier, which is being used by A, correctly
Reason Three: constraint of power. Portable devices' activity reply very much on battery life.
MAC Solutions:
CSMA/CA: To solve the "near/far" problem, 802.11 uses a slightly modified protocol known as Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) or the Distributed Coordination Function (DCF).
CSMA/CA works as follows. A station wishing to transmit senses the air, and, if no activity is detected, the station waits an additional, randomly selected period of time and then transmits if the medium is still free.
CSMA/CA reduces the probability that two or more stations will begin transmitting at the same time and ensures some degree of fairness.
But, CSMA/CA can not guarantee that collision does not happen. Thus, 802.11 uses explicit acknowledgement (ACK) to ensure transmission correctness. An ACK packet is sent by the receiving station to confirm that the data packet arrived intact. If the packet is received intact, the receiving station issues an ACK frame that, once successfully received by the sender, completes the process. If the ACK frame is not detected by the sending station, either because the original data packet was not received intact or the ACK was not received intact, a collision is assumed to have occurred and the data packet is transmitted again after waiting another random amount of time.
CSMA/CA thus provides a way of sharing access over the air. This explicit ACK mechanism also handles interference and other radio-related problems very effectively. However, it does add some overhead to 802.11 that 802.3 does not have, so that an 802.11 LAN will always have slower performance than an equivalent Ethernet LAN.
RTS/CTS protocol: To address the "hidden node" issue, 802.11 specifies an optional Request to Send/Clear to Send (RTS/CTS) protocol at the MAC layer. When this feature is in use, a sending station transmits an RTS and waits for the access point to reply with a CTS. Since all stations in the network can hear the access point, the CTS causes them to delay any intended transmissions, allowing the sending station to transmit and receive a packet acknowledgment without any chance of collision. Since RTS/CTS adds additional overhead to the network by temporarily reserving the medium, it is typically used only on the largest-sized packets, for which retransmission would be expensive from a bandwidth standpoint.
Security:
IEEE 802.11 provides for security via two methods: authentication and encryption. Authentication is the means by which one station is verified to have authorization to communicate with a second station in a given coverage area. In the infrastructure mode, authentication is established between an AP and each station.
802.11 provides two methods of authentication: open system or shared key. An open system allows any client to authenticate as long as it conforms to any MAC address filter policies that may have been set. All authentication packets are transmitted without encryption. Shared key authentication, on the other hand, requires WEP be enabled, and identical WEP keys on the client and AP (for more information on WEP keys, see below). The initiating endpoint requests a shared key authentication, which returns unencrypted challenge text (128 bytes of randomly generated text) from the other endpoint. The initiator encrypts the text and returns the data.
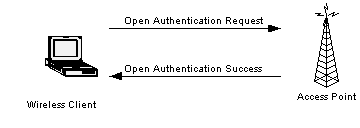
Fig.4 Open Authentication
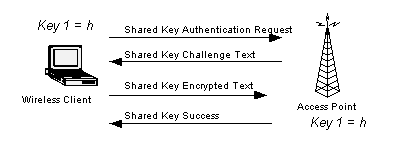
Fig.5 Shared Key Authentication
Encryption is intended to provide a level of security comparable to that of a wired LAN. The Wired Equivalent Privacy (WEP) feature uses the RC4 PRNG algorithm from RSA Data Security Inc. According to the protocol, WEP generally uses a 64-bit RC4 stream cipher (see information on 128-bit below). RC4 is a symmetric encryption algorithm, meaning the same key is used to both encrypt and decrypt the data payload. This encryption key is generated from a seed value created by combining a 40-bit user defined WEP key with a 24-bit Initialization Vector (IV). The WEP key generally takes the form of a 10-character hexadecimal string (0-9,A-F) or a 5-character ASCII string, which must be present on both ends of the wireless transmission. The protocol allows for up to four concurrently defined WEP keys.
The standard does not, however, currently define how the IV is established, so the implementation varies by vendor. When an encrypted wireless client starts transmitting data, the IV can start with a value of zero or another randomly defined starting value, and generally increments upwards in a predictable manner, with each successive frame. However, some vendors (such as Cisco) use a more sophisticated, random determination of the IV.
Although not yet part of the protocol specification, many 802.11b vendors also support 128-bit RC4 encryption. This requires a 104-bit WEP key (26 character hexadecimal or 13 character ASCII), but uses the same 24-bit IV value. The figure below shows that the 128-bit encrypted implementations from several vendors are interoperable despite the lack of a standard.
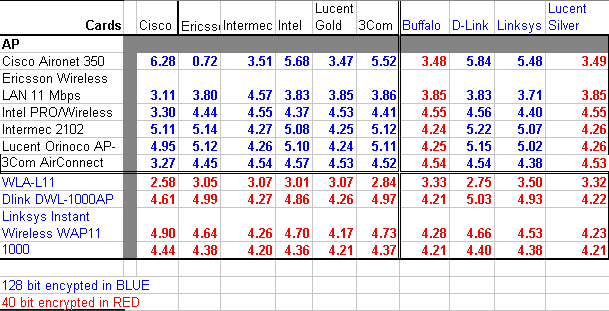
Fig.6 Wireless Performance numbers (from Previously undisclosed performance numbers provided by PC Magazine, Volume 21 Issue 5. All values reported in Mbps.)
Other robustness features provided in 802.11 MAC
Finally, the 802.11 MAC layer provides some other robustness features:
CRC checksum: Each packet has a CRC checksum calculated and attached to ensure that the data was not corrupted in transit. This is different from Ethernet, where higher-level protocols such as TCP handle error checking.
Packet fragmentation: allows large packets to be broken into smaller units when sent over the air, which is useful in very congested environments or when interference is a factor, since larger packets have a better chance of being corrupted. This technique reduces the need for retransmission in many cases and thus improves overall wireless network performance. The MAC layer is responsible for reassembling fragments received, rendering the process transparent to higher-level protocols.
Roaming Provisions: 802.11 allows a client to roam among multiple APs that can be operating on the same or separate channels. But this feature is perhaps least defined features discussed. The standard does identify the basic message formats to support roaming, but everything else is left up to network vendors. In order to fill the void, the Inter-Access Point Protocol (IAPP) was jointly developed by Aironet, Lucent Technologies, and Digital Ocean. Among their things, IAPP extends nulti-vendor interoperability to the roaming function. It addressed roaming within a single ESS and between two or more ESSs.
Support for Time-Bounded Data: Time-bounded data such as voice and video is supported in the 802.11 MAC specification through the Point Coordination Function (PCF). As opposed to DCF, where control is distributed to all stations, in PCF mode a single access point controls access to the media. If a BSS is set up with PCF enabled, time is spliced between the system being in PCF mode and in DCF (CSMA/CA) mode. During the periods when the system is in PCF mode, the access point will poll each station for data, and after a given time move on to the next station. No station is allowed to transmit unless it is polled, and stations receive data from the access point only when they are polled. Since PCF gives every station a turn to transmit in a predetermined fashion, a maxium latency is guaranteed. A downside to PCF is that it's not particularly scalable, in that a single point needs to have control of media access and must poll all stations, which can be ineffective in large networks.
Power Management: To extend the battery life of portable devices, 802.11 supports two power- utilization modes, called Continuous Aware Mode and Power Save Polling Mode. In the former, the radio is always on and drawing power, whereas in the latter, the radio is "dozing" with the AP queueing any data for it. The client radio will wake up periodically in time to receive regular beacon signals from the AP, The beacon includes information regarding which stations have traffic waiting for them, and the client can thus awake upon beacon notification and receives its data, returning to sleep forward. 802.11 also specified that APs include buffers to queue messages to support sleeping clients. APs are permitted to dump unread messages after a specified time passes.